Setting up Multiple GitHub Deploy Keys
A common way of accessing repositories through GitHub is with the use of an ssh key. This ssh key is set in your account settings and is responsible for authenticating any requests you make.
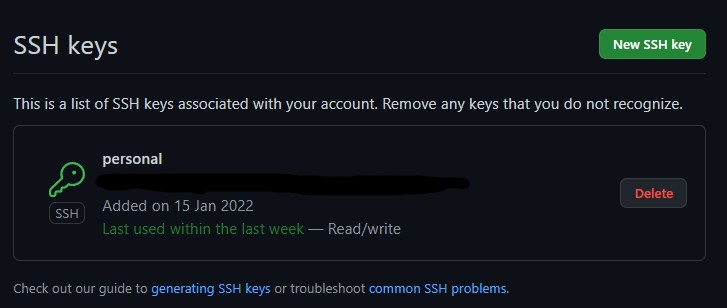
Since this ssh key allows you to perform any privileged action that your account is able to, it is important to keep your ssh private key secret. During the development process, this private ssh key is likely kept safe on your personal computer. But what happens when you want to deploy your repo to an external server?
This is where deploy keys shine. Deploy keys are also just ssh keys BUT they only allow access to a single repo. They can be even further restricted by only allowing read access. This would be useless for a development environment, but for a server where all we will be doing is cloning and pulling changes? It's perfect.
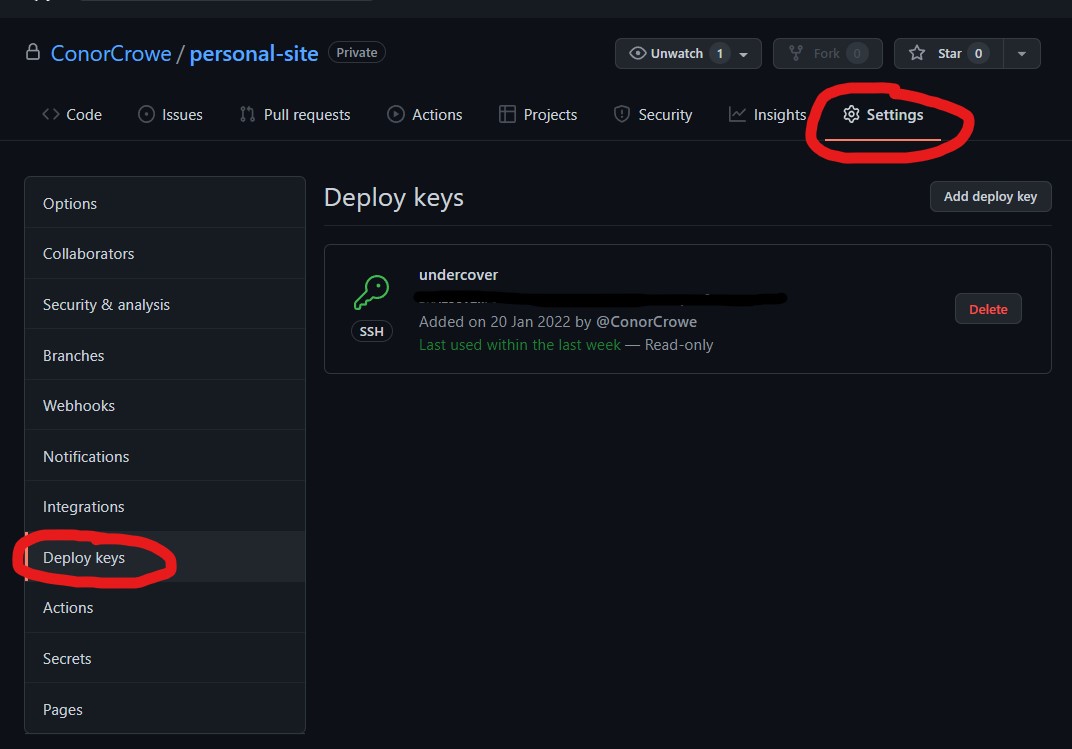 |
|---|
| Deploy keys can be set in your repo settings page. For how to generate ssh keys follow this guide. |
With a deploy key set, you can access your repo the same as you normally would using a command like git clone git@github.com:ConorCrowe/personal-site.git
This works perfectly when you are only using a single repository for your application. You will start to run into issues if you have a multirepo set up. This is because you can't use the same deploy key for multiple repos - the almighty Github gods won't allow it.
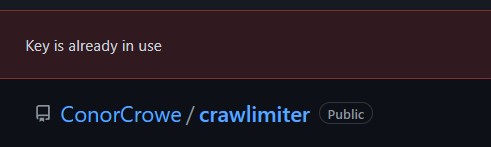 |
|---|
| GitHub says no |
The workaround is to just set up a unique key for each of your repos. Now, the problem is that you have a seperate key to use for each repo but the git cli has no way to actually set which key to use. This means that your git clone commands will likely authenticate with the wrong key and fail as a result.
In order to set the deploy key for each git command you can use ssh config. By default, the ssh config file is placed in the users home directory .ssh folder. e.g. ~/.ssh/config.
Step by Step
I will now go through step by step for how I set up deploy keys for my 3 repo application.
-
Generate ssh keys with unique name for each repo and set the deploy keys on GitHub.
-
On your deployment server Run
touch ~/.ssh/configand then open the file with the text editor of your choice.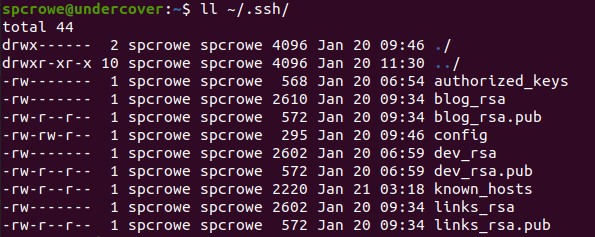
Sample .ssh folder -
For each repo add a Host entry to the config file as below. The first line is the unique identifier that you will use. HostName will be github.com for all. IdentifyFile will be the path to the specific private key you want to use. IdentitiesOnly just means ssh-agent will not try keys for this host other than the one specified in this config.
Host github.com-site HostName github.com IdentityFile ~/.ssh/dev_rsa IdentitiesOnly yes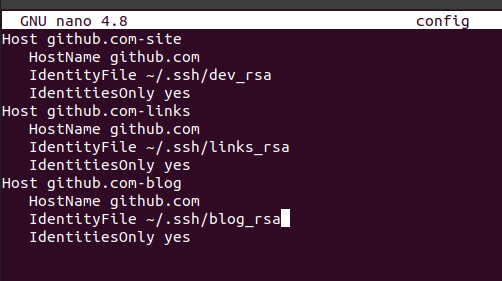
my ssh config with 3 deploy keys -
Finally, when cloning your repos for the first time use the custom Host you specified to replace github.com.
i.e.
git clone git@github.com:ConorCrowe/personal-site.git
becomes
git clone git@github.com-site:ConorCrowe/personal-site.gitThe other two repos:
git clone git@github.com-links:ConorCrowe/links.git
git clone git@github.com-blog:ConorCrowe/blog-posts.git
Why this works
This works because git interfaces with the system's ssh client when performing ssh authentication. The ssh client then performs a lookup on the provided hostname and uses the options we defined in our ssh config. Additionally, Git then saves the repo's remote origin with our custom hostname. This means in the future we can just do git pull without specifying the remote address and this lookup magic will all happen seamlessly in the background.
Conclusion
With a little bit of extra work it is possible to securely set up deploy keys for a multirepo application. Doing this helps us to avoid potentially leaking our oh so valuable personal ssh key and giving full control of our GitHub account.